Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) offers real-time monitoring and analysis of events as well as tracking and logging of security data for compliance or auditing purposes.
The Challenge
It is becoming quite evident that cyber-crimes are increasing daily. Attackers have become more sophisticated and dangerous and their appropriate and timely detection has become a real challenge. Examples of current cybersecurity incidents affecting IT and ICT are ransomware attacks; malware having impact on the utility’s ability to conduct business and operations; phishing campaigns directed to executives, executive assistants, SCADA engineers, IT administrators or other privileged users; business email compromise incidents, including account takeover or impersonation of executives; data leakage and thefts; social engineering to gather sensitive information from personnel.
The Solution
SIEM is a security solution that helps organizations recognize potential security threats and vulnerabilities before they have a chance to disrupt business operations
SIEM
Gain Comprehensive, Centralized
Visibility
Security information and event management (SIEM) tools collect and aggregate log and event data to help identify and track breaches. SIEM enables organizations to gain centralized, comprehensive visibility into siloed environments by collecting, parsing and normalizing both log and flow data.
What Is Security Information and Event Management (SIEM)?
security information and event management (SIEM) is software that improves security awareness of an IT environment. SIEM offers real-time monitoring and analysis of events as well as tracking and logging of security data for compliance or auditing purposes.
Put simply, SIEM is a security solution that helps organizations recognize potential security threats and vulnerabilities before they have a chance to disrupt business operations.
SIEM tools provide:
- Real-time visibility across an organization’s information security systems.
- Event log management that consolidates data from numerous sources.
- A correlation of events gathered from different logs or security sources, using if-then rules that add intelligence to raw data.
- Automatic security event notifications. Most SIEM systems provide dashboards for security issues and other methods of direct notification.
SIEM works by combining two technologies:
- Security information management (SIM), which collects data from log files for analysis and reports on security threats and events, and
- security event management (SEM), which conducts real-time system monitoring, notifies network admins about important issues and establishes correlations between security events.
How does Security Information and Event Management (SIEM) work?
SIEM’s core function is threat detection and threat management. A SIEM supports the incident response capabilities of a Security Operations Center (SOC), which includes threat detection, investigation, threat hunting, and response and remediation activities.
SIEM tools work by gathering event and log data created by servers, end-user devices, networking equipment, applications, and security devices, such as antivirus filters and firewalls, throughout a company’s infrastructure and bringing that data together on a centralized platform. The SIEM tools identify and sort the data into such categories as successful and failed logins, malware activity and other likely malicious activity.
SIEM systems ingest and interpret logs from as many sources as possible including:
- Firewalls/unified threat management systems (UTMs)
- Intrusion detection systems (IDS) and intrusion prevention systems (IPS)
- Web filters
- Endpoint security
- Wireless access points
- Routers
- Switches
- Application servers
- Honeypots
The SIEM software then generates security alerts when it identifies potential security issues. Using a set of predefined rules, organizations can set these alerts as low or high priority.
For instance, a user account that generates 25 failed login attempts in 25 minutes could be flagged as suspicious but still be set at a lower priority because the login attempts were probably made by the user who had probably forgotten his login information.
However, a user account that generates 130 failed login attempts in five minutes would be flagged as a high-priority event because it’s most likely a brute-force attack in progress.
While SIEM solutions vary in capability, most offer the same core set of functionality:
What are The Benefits of Security Information and Event Management (SIEM)?
Regardless of how large or small your organization may be, taking proactive steps to monitor for and mitigate IT security risks is essential. SIEM solutions benefit enterprises in a variety of ways and have become a significant component in streamlining security workflows. Some of the benefits include:
Advanced real-time threat recognition
SIEM active monitoring solutions across your entire infrastructure significantly reduces the lead time required to identify and react to potential network threats and vulnerabilities, helping to strengthen security posture as the organization scales.
Regulatory compliance auditing
SIEM solutions enable centralized compliance auditing and reporting across an entire business infrastructure. Advanced automation streamlines the collection and analysis of system logs and security events to reduce internal resource utilization while meeting strict compliance reporting standards.
Detecting Advanced and Unknown Threats
Considering how quickly the cybersecurity landscape changes, organizations need to be able to rely on solutions that can detect and respond to both known and unknown security threats. Using integrated threat intelligence feeds and AI technology, SIEM solutions can successfully mitigate against modern-day security breaches such as:
- Insider threats – Security vulnerabilities or attacks that originate from individuals with authorized access to company networks and digital assets. These attacks could be the result of compromised credentials.
- Phishing attacks – Social engineering attacks masquerading as trusted entities, often used to steal user data, login credentials, financial information, or other sensitive business information.
- SQL Injections – Malicious code executed via a compromised webpage or application designed to bypass security measures and add, modify, or delete records in an SQL database.
- DDoS Attacks – A Distributed-Denial-of-Service (DDoS) attack designed to bombard networks and systems with unmanageable levels of traffic, degrading performance of websites and servers until they are unusable.
- Data exfiltration – Data theft or extrusion is commonly achieved by taking advantage of common or easy-to-crack passwords on network assets, or through the use of an Advanced Persistent Threat, or APT.
Conducting Forensic Investigations
SIEM solutions are ideal for conducting digital forensic investigations once a security incident occurs. SIEM solutions allow organizations to efficiently collect and analyze log data from all of their digital assets in one place. This gives them the ability to recreate past incidents or analyze new ones to investigate suspicious activity and implement more effective security processes.
Assessing and Reporting on Compliance
Compliance auditing and reporting is both a necessary and challenging task for many organizations. SIEM solutions dramatically reduce the resource expenditures required to manage this process by providing real-time audits and on-demand reporting of regulatory compliance whenever needed.
Monitoring Users and Applications
With the rise in popularity of remote workforces, SaaS applications and BYOD (Bring Your Own Device) policies, organizations need the level of visibility necessary to mitigate network risks from outside the traditional network perimeter. SIEM solutions track all network activity across all users, devices, and applications, significantly improving transparency across the entire infrastructure and detecting threats regardless of where digital assets and services are being accessed.
SIEM Implementation Best Practices
Before or after you’ve invested in your new solution, here are some SIEM implementation best practices you should follow:
- Begin by fully understanding the scope of your implementation. Define how your business will best benefit from deployment and set up the appropriate security use cases.
- Design and apply your predefined data correlation rules across all systems and networks, including any cloud deployments.
- Identify all of your business compliance requirements and ensure your SIEM solution is configured to audit and report on these standards in real-time so you can better
- Understand your risk posture.
- Catalog and classify all digital assets across your organization’s IT infrastructure. This will be essential when managing collecting log data, detecting access abuses, and monitoring network activity.
- Establish BYOD (Bring Your Own Device) policies, IT configurations, and restrictions that can be monitored when integrating your SIEM solution.
- Regularly tune your SIEM configurations, ensuring you’re reducing false positives in your security alerts.
- Document and practice all incident response plans and workflows to ensure teams are able to respond quickly to any security incidents that require intervention.
- Automate where possible using artificial intelligence (AI) and Security Orchestration, Automation, and Response (SOAR) capabilities.
- Evaluate the possibility of investing in an MSSP (Managed Security Service Provider) to manage your SIEM deployments. Depending on the unique needs of your business, MSSPs may be better equipped to handle the complexities of your SIEM implementation as well as regularly manage and maintain its continuous functionality.
How To Get The Most From SIEM Security Solutions?
In a traditional security operations centre, incident response processes followed by cybersecurity teams around the world are often standard and can take hours. SOAR automates workflows and accelerates threat qualification, investigation, and response which reduces response times by automating large parts of the process which helps security teams prioritize real threats. It does this by interacting with other security technologies to automatically carry out the initial steps of incident response
IBM and SIEM
When it comes to Security Information and Event Management, it’s important to invest in a SIEM solution you can trust from a provider that understands the importance of strengthening enterprise security posture.
IBM Security QRadar SIEM is a comprehensive security intelligence platform designed to help organizations manage all the complexities of their security operations processes from one unified platform.
What Are IBM QRadar SIEM Benefits?
Available as an on-premises, cloud or SaaS solution, QRadar offers flexible deployment options for today’s evolving businesses to deploy security where it is needed most. Featuring advanced analytics, AI-driven investigations, real-time threat detection, and comprehensive IT compliance management, QRadar has all the capabilities your business needs to detect, investigate, prioritize, and respond threats across your entire organizaiton while ensuring your business continuity.
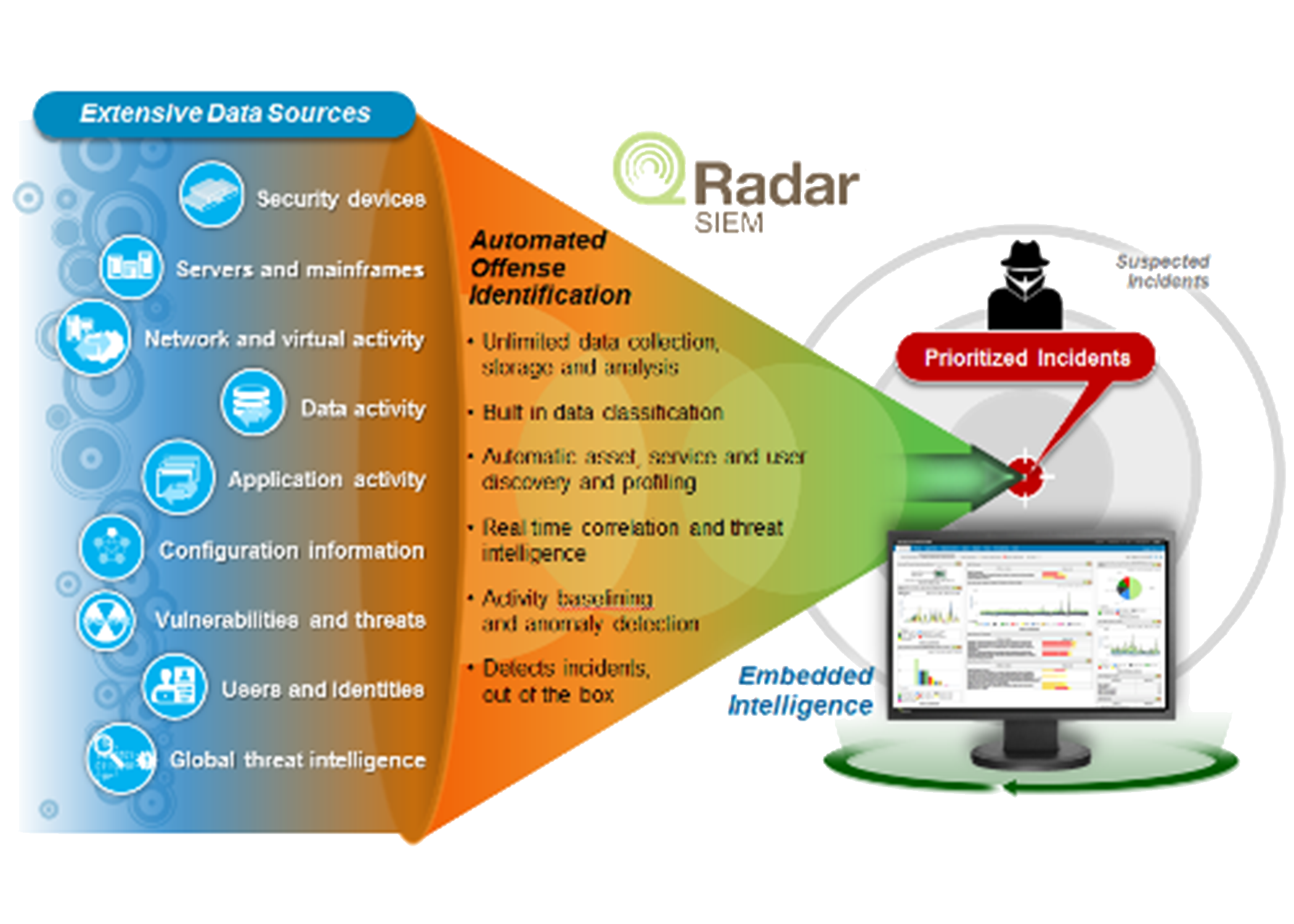
Automate Security Intelligence To Rapidly Detect Threats
IBM QRadar SIEM is designed to automatically analyze and correlate activity across multiple data sources including logs, events, network flows, user activity, vulnerability information and threat intelligence to identify known and unknown threats.
OFFERINGS

Our engineers and consultants can assist in implementation and preparation of IBM QRadar SIEM that collect log events and network flow data from cloud-based applications.




