Hardware Security Modules (HSM)
Hardware Security Modules (HSM) offer protection to your most sensitive data, control access and limit risk to your company’s sensitive private keys.
The Challenge
Today, businesses collect and store sensitive data of customers like credit card information, banking details, health records, etc. The misuse of these hypersensitive data could lead to a digital doomsday. This information about customers is often stored in devices and on servers.
Sometimes, even the encrypted data are leaked because the private key gets stolen or hacked.
The Solution
Companies need Hardware Security Modules (HSM) to make data invulnerable to leaks or tampering.
HSM
HSMs are an
investment and often well worth the cost
With tightly controlled access and specialized hardware, an HSM is necessary for many industries to maintain security and compliance, as well as to practice and maintain strong key management practices for your data.
What is a Hardware Security Module (HSM)?
A hardware security module (HSM) is a physical device that provides extra security for sensitive data. Hardware security modules (HSMs) are hardened, tamper-resistant hardware devices that secure cryptographic processes by generating, protecting, and managing keys used for encrypting and decrypting data and creating digital signatures and certificates.
It acts as an invaluable resource for performing all sorts of cryptographic operations without exposing them on a network vulnerable to hacking attempts by malware or other malicious software programs. HSM could be a dedicated hardware system, inbuilt hardware, or just a plugin device.
HSM has repeatedly proven its ability to secure and manage digital keys, digital signatures, and other encrypted documents. It performs encryption and decryption of documents to ensure the highest level of confidentiality and protection.
HSMs are tested, validated and certified to the highest security standards including FIPS 140-2 and Common Criteria.
Why Should You Use A Hardware Security Module (HSM)?
HSM is an isolated cryptographic engine that can secure, generate, and manage cryptographic keys for various purposes. The use of HSMs is virtually unlimited, depending on the needs and scale of operation. Hardware security module in an organization can be used to:
- Protect hardware devices from unauthorized access or penetration attacks
- Reduce the number of security incidents related to lost or stolen tokens
- Ensure regulatory compliance related to data security like HIPAA, eIDAS, UIDAI, etc.
- Separate cryptographic functions from regular operations
- Authorize and authenticate the critical cryptographic transfer
- Ensure the protection of cryptographic keys
- Permanently delete private keys to ensure non-recovery
The HSMs can be used to secure data that is beyond your premise. HSM generated certificates can help in Remote device authentication. HSM generated keys are best to be used to secure data in cloud. These keys can be securely transferred to cloud (eg: Azure, AWS, GCP) and can be used with security applications.
How are HSMs used?
Any business that handles valuable or sensitive information should consider using a hardware security module. That type of information includes credit or debit card data, intellectual property, customer data and employee information.
HSMs secure data generated by a range of applications, including the following:
- websites
- banking
- mobile payments
- cryptocurrencies
- smart meters
- medical devices
- identity cards and personal identification numbers (PINs)
- digital documents
HSM devices are also used for several purposes, including digital signing, key generation and management, ensuring compliance, simplifying audits, and securing data and digital identities.
What Does a Hardware Security Module Do?
With the rise in cyberattacks and data breaches, protecting your sensitive information is more critical than ever. Hardware Security Module does the following to ensure a higher level of security:
- Generates protects and manages private key including Root CA Key for PKI implementation
- Supports certified implementations of leading data encryption algorithms like RSA, ECC, AES etc.
- Provides functions to securely generate the certificate revocation list (CRL)
- Authenticates users and devices through digital certificates generated securely using HSMs
- Generates, manages and deletes the keys needed for the cryptography process
- Protects cryptographic keys and handles encryption and decryption processes
- Helps organizations to meet existing and emerging regulatory compliances like UIDAI, CCA, HIPAA, eIDAS, GDPR etc.
HSM in The Real World
With wide-ranging use, many industries and businesses have come to rely on HSM devices to provide quick, safe and secure data transactions and verification. Whatever the use case may be, the key elements of any HSM device require that it:
- Is designed using specialized hardware which is well-tested and certified.
- Has a security-oriented Operating System.
- Has access to a network interface controlled by strict internal parameters.
- Actively stores and protects cryptographic material.
Any programmer would normally mix the database access code, business-logic and cryptographic calls in one single application, leaving it dangerously vulnerable to exploitation and attack. This is a dangerous approach, as an attacker can leverage crafted data to access cryptographic materials, steal keys, install an arbitrary certificate, and so on.
To prevent such intrusions, HSM devices require two separate operational zones. A single one that holds the business logic, and a second for cryptography which is entrusted with the cryptographic operation.
How HSMs Improve IT and Data Security?
There are also many other purposes and uses that HSMs serve in terms of PKI and general cybersecurity. You can use an HSM to:
- Store and protect all of your cryptographic keys throughout their lifecycles. HSMs are generally standalone network-connected devices that are separate from your servers. This helps to keep your keys secure through all lifecycle stages — from generation all the way through their eventual destruction or revocation.
- Generate the most cryptographically strong keys for your PKI. HSMs have built-in true random number generators (TRNGs) that provide randomness and unpredictability.
- Protect the security of your keys through “zeroization.” Because HSMs are tamper-resistant devices (both for logical and physical attacks), they’re built to erase or destroy all stored cryptographic data to prevent compromise.
- Secure your organization’s cryptographic operations and services. Restricting these functions (such as signing PKI certificates, applications and documents) to occur only within the secure, stand-alone environment of the HSM helps to prevent key exposure.
- Improve server performance via load balancing. HSM devices are stripped-down, standalone devices that can take on the responsibility of performing operations that otherwise bog down your servers. Some HSMs are equipped to act as web traffic accelerators by offloading cryptographic operations.
- Protect your keys from insecure extractions that can lead to compromise. “Wrap” or encrypt your encryption keys to prevent them from being extracted in plaintext format.
- Secure the keys for your development, testing and production environments. An HSM protects the private PKI keys used by the software and systems relating to your internal production and testing environments so these systems can use them without needing direct access to them. (Note: use a separate HSM for each environment to avoid data security risks — never use the same HSM across multiple environments).
- Ensure compliance with data security regulations and simplify audit processes. HSMs are typically validated hardware components that ensure compliance because they meet specific industry standards. They also provide tamper-resistant logs that inform you about:
- what cryptographic operations they’re used to perform,
- when these operations were carried out, and
- who was responsible for authorizing those operations.
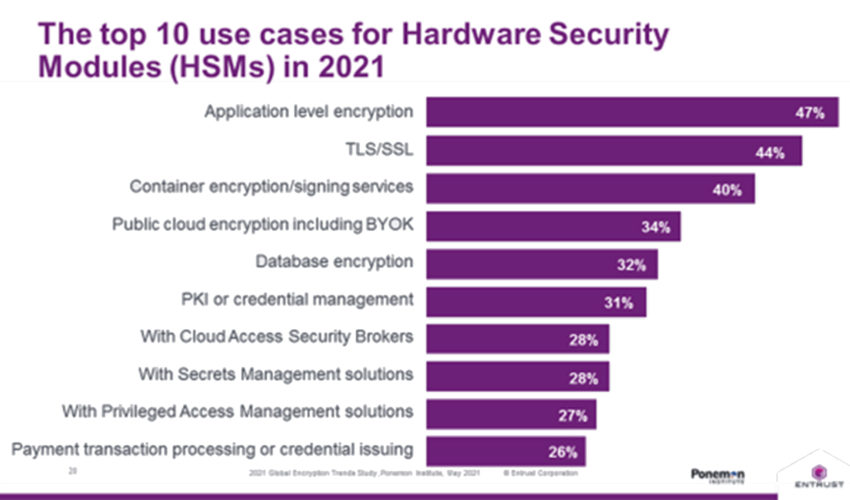
HSM Use Cases
Here are some successful examples of hardware security modules implementation.
Use Case 1: Protecting Private Key
Problem: Digital signatures rely on encryption and decryption through private and public keys for identity verification. In case a private key of an organization or individual is hacked, it defies the whole digital signature concept.
Solution: The HSM module stores all the private keys in a highly secured, tamper-free environment. It generates truly random session keys, manages them, and permanently deletes them once their purpose is over.
Use Cases 2: Offloading Workload from Web Servers
Problem: Web servers and their clients use SSL or TLS to establish a secure connection. In this process, the web server’s identity is confirmed through public-private key pairs that are mathematically encrypted together. This requires a lot of processing which makes the web servers slow.
Solution: HSM could be used to offload some of the computation on cloud clusters. It reduces the processing need of webservers and adds an extra layer of security by storing the server’s private key.
Use Case 3: Mobile Device Management for Remote Devices
Problem: It was challenging to create trusted certificate provisioning to access remote employees’ networks. The work from home and BYOD culture resulted in severe security issues.
Solution: HSM creates unique identities of devices and issues keys and certificates by PKI even on the cloud. HSM leverages transparent and secures mobile device management to ensure secured access. The simple device enrolment process can manage and confirm the identities of all the employee’s devices.
OFFERINGS

Entrust is a leading global provider of HSMs with the nShield General Purpose HSM product family.
Using Entrust nShield HSMs, IT organizations can address key security objectives and compliance mandates. Whether you’re looking to protect your sensitive encryption keys or address compliance mandates that call for the use of HSMs, Entrust can help.




