Endpoint Detection and Response (EDR)
Today’s endpoint protection systems are designed to quickly detect, analyze, block, and contain attacks in progress. To do this, they need to collaborate with each other and with other security technologies to give administrators visibility into advanced threats to speed detection and remediation response times.
The Challenge
Advanced attacks can take just minutes—if not seconds—to compromise endpoints. The continued growth of advanced attacks and ransomware, along with the lack of shared intelligence among disparate security products, results in a slower, less effective endpoint threat detection, response and endpoint security.
The Solution
EDR is designed to provide comprehensive endpoint protection against cyber threats.
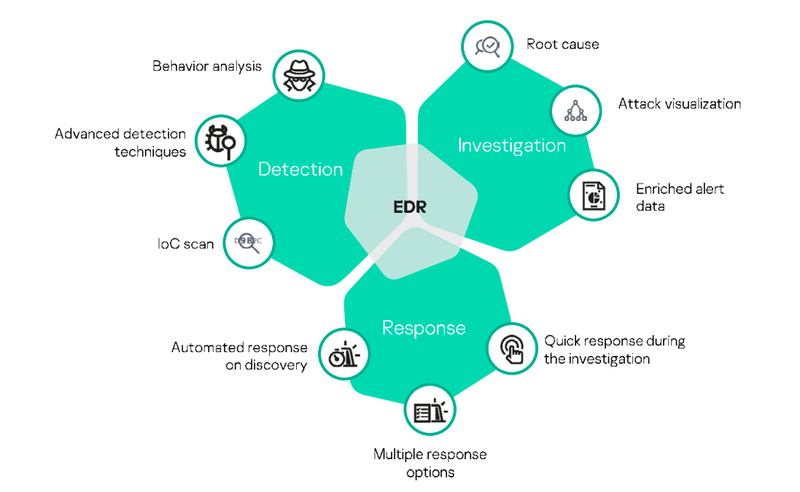
EDR
Endpoint Detection and
Response (EDR) Security Is More Crucial Than Ever
By providing visibility into your endpoints, EDR solutions can help you detect threats that other endpoint security measures may have missed.
What is endpoint security?
Endpoint security is the practice of securing endpoints or entry points of end-user devices such as desktops, laptops, and mobile devices from being exploited by malicious actors and campaigns. Endpoint security systems protect these endpoints on a network or in the cloud from cybersecurity threats. Endpoint security has evolved from traditional antivirus software to providing comprehensive protection from sophisticated malware and evolving zero-day threats.
What is endpoint detection and response (EDR)?
EDR is a solution deployed on endpoint devices to prevent file-based malware attacks, to detect and block malicious activity from trusted and untrusted applications, and to provide the investigation and remediation capabilities needed to dynamically respond to security incidents and alerts.
What’s considered an endpoint?
Endpoints can range from the more commonly thought of devices such as:
- Laptops
- Tablets
- Mobile devices
- Smart watches
- Printers
- Servers
- ATM machines
- Medical devices
If a device is connected to a network, it is considered an endpoint. With the growing popularity of BYOD (bring your own device) and IoT (Internet of Things), the number of individual devices connected to an organization’s network can quickly reach into the tens (and hundreds) of thousands.
Why endpoint security is important?
An endpoint protection platform is a vital part of enterprise cybersecurity for a number of reasons. First of all, in today’s business world, data is often the most valuable asset a company has—and to lose that data, or access to that data, could put the entire business at risk of insolvency. Businesses have also had to contend with not only a growing number of endpoints, but also a rise in the number of types of endpoints. These factors make enterprise endpoint security more difficult on their own, but they’re compounded by remote work and BYOD policies—which make perimeter security increasingly insufficient and create vulnerabilities. The threat landscape is becoming more complicated, too: Hackers are always coming up with new ways to gain access, steal information or manipulate employees into giving out sensitive information. Add in the opportunity cost of reallocating resources from business goals to addressing threats, the reputational cost of a large-scale breach, and the actual financial cost of compliance violations, and it’s easy to see why endpoint protection platforms have become regarded as must-haves in terms of securing modern enterprises.
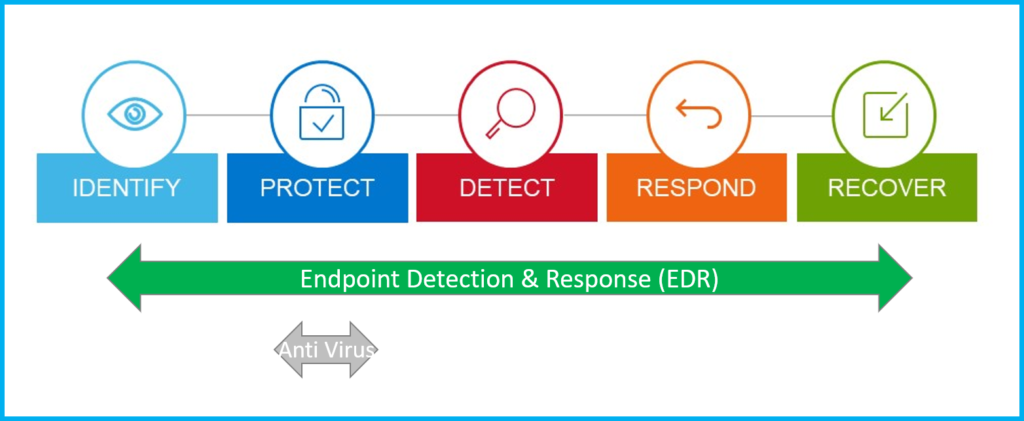
What is the difference between EDR and a traditional Anti-virus?
EDR protects endpoints from being breached – no matter if they are physical or virtual, on- or off-premise, in data centers or in the Cloud. It is installed on laptops, desktops, servers, virtual machines, as well as remote endpoints themselves.
Antivirus is often part of an endpoint security solution and is generally regarded as one of the more basic forms of endpoint protection. Instead of using advanced techniques and practices, such as threat hunting and endpoint detection and response (EDR), antivirus simply finds and removes known viruses and other types of malware . Traditional antivirus runs in the background, periodically scanning a device’s content for patterns that match a database of virus signatures. Antivirus is installed on individual devices inside and outside the firewall.
Endpoint detection and response (EDR) and traditional antivirus solutions differ in some key ways.
Endpoint Security vs. Network Security:
Antivirus programs are designed to safeguard a single endpoint, offering visibility into only that endpoint, in many cases only from that endpoint. Endpoint security software, however, looks at the enterprise network as a whole and can offer visibility of all connected endpoints from a single location.
Administration:
Legacy antivirus solutions relied on the user to manually update the databases or to allow updates at pre-set time. EPPs offer interconnected security that moves administration responsibilities to enterprise IT or cybersecurity team.
Protection:
Traditional antivirus solutions used signature-based detection to find viruses. This meant that if your business was Patient Zero, or if your users hadn’t updated their antivirus program recently, you could still be at risk. By harnessing the cloud, today’s EDR solutions are kept up to date automatically. And with the use of technologies such as behavioral analysis, previously unidentified threats can be uncovered based suspicious behavior.
How does Endpoint Detection and Response (EDR) work?
EDR solutions work by identifying a security incident and help security teams mitigate it. The process typically involves the following steps:
- Monitor endpoints— ongoing monitoring of all endpoint devices.
- Use behavioral analysis to detect anomalies— establish a behavioral baseline for each device, detect activity that diverges from normal patterns, and detect when it exceeds and acceptable threshold and is probably malicious.
- Quarantines affected endpoints and processes— as soon as a security incident is discovered, automatically isolate the endpoint device and stop suspicious processes running on it.
- Trace back to the attacker’s original point of entry— compiles data on the potential entry points for an attack, providing more context beyond the activity on the current endpoint.
- Provide information about the anomaly and suspected breach— provide analysts with everything they need to investigate the incident.
What are the components of Endpoint Detection and Response (EDR)?
Typically, endpoint security solution includes these key components:
- Machine-learning classification to detect zero-day threats in near real time
- Advanced antimalware and antivirus protection to protect, detect, and correct malware across multiple endpoint devices and operating systems
- Proactive web security to ensure safe browsing on the web
- Data classification and data loss prevention to prevent data loss and exfiltration
- Integrated firewall to block hostile network attacks
- Email gateway to block phishing and social engineering attempts targeting your employees
- Actionable threat forensics to allow administrators to quickly isolate infections
- Insider threat protection to safeguard against unintentional and malicious actions
- Centralized endpoint management platform to improve visibility and simplify operations
- Endpoint, email and disk encryption to prevent data exfiltration